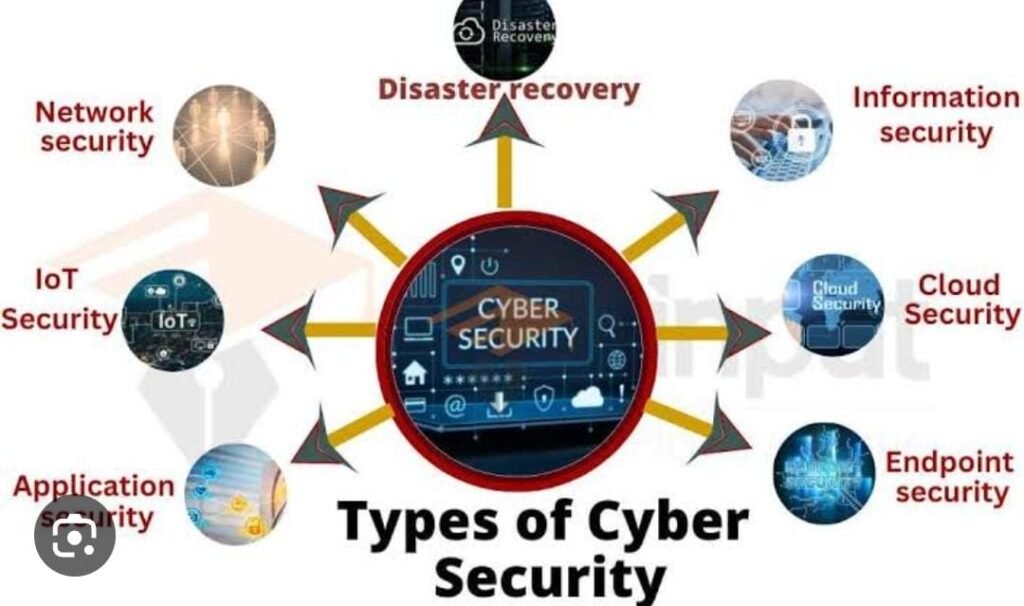
It’s crucial for both businesses and users to grasp the five types of cyber security to safeguard their data from malicious entities. Implementing these measures effectively ensures not just data protection but also the uninterrupted flow of business operations. In today’s digital world, keeping your online stuff safe is really, really important.
This guide is like your best friend, showing you step-by-step how to make sure your online life is secure. It covers all the important things and gives you smart tips to make your defenses strong. Jump into this guide, and you’ll not just understand but also be able to do things that keep you safe from all those tricky online problems. Let’s make your online world safe and sound together!

In the dynamic realm of cybersecurity, safeguarding digital assets requires a multifaceted approach. This blog post will delve into five crucial types of cybersecurity measures, providing both SEO-friendly insights and user-friendly tips for enhancing your digital defenses.
“What is cyber security?”
“As the first line of defense, endpoint security plays a pivotal role in protecting individual devices from various cyber threats. Delve into the significance of robust endpoint protection and grasp its integral role in strengthening the security of your digital ecosystem effectively.”
Cyber security: Exploring Five Essential Types
In the dynamic domain of cybersecurity, ensuring the protection of digital assets necessitates a comprehensive strategy. This blog post delves into five critical cybersecurity measures, offering SEO-friendly insights and user-friendly tips to enhance your digital defenses effectively.
Endpoint Security
Endpoint Security takes center stage, defending individual devices against the myriad threats lurking in the digital shadows. This section not only illuminates the significance of endpoint protection but also provides practical insights for implementing effective safeguards.
Network Security
Picture Network Security as a digital superhero, always protecting our online world from tricky cyber threats. This guide is a friendly tour through the complex world of cybersecurity, helping you understand the important parts that make a strong defense.
Picture resilient firewalls as tough walls and encryption as locks with secret codes. Come along with us. We exploring these tools that make a super-strong shield. This journey makes sure our online world stays safe and secure, like a trustworthy sanctuary even when cyber threats keep changing.
Cloud Security
Imagine your data as a traveler seeking refuge in the vast expanse of the cloud. Cloud Security acts as a vigilant guardian, ensuring our information’s safety in the virtual realm. Let’s simplify its importance – it’s a set of tools and practices keeping our data secure up there.
Encryption, a fancy term for digital locks, ensures that only authorized parties can access our information. It’s like having a secret code to open the door – making sure our data stays private. Access controls act as gatekeepers, allowing only the right people to enter our virtual space. Think of it as having a bouncer at the entrance of a party, letting in only the invited guests.
Identity and Access Management
IAM is like the digital gatekeeper, controlling who gets into the important parts of our online world. It’s not just about blocking or allowing – it goes deeper. With things like multi-factor authentication (more than just a password) and role-based controls (giving specific permissions), IAM becomes a superhero, making sure our digital identity is super secure. These smart tools create a strong defense, making sure only the right people can travel through the digital world we call our own.
Behavioral Analytics
Behavioral Analytics, driven by the prowess of machine learning, pioneers a proactive strategy by meticulously identifying unusual patterns in user behavior. This advanced approach serves as a game-changer, exponentially amplifying our capacity to detect and neutralize potential threats within the expansive digital realm. Join us in exploring the sophisticated intricacies of how this cutting-edge system not only fortifies our overall cybersecurity but also establishes a formidable defense, ensuring the utmost security and resilience against the ever-evolving landscape of online threats.
Conclusion
In conclusion, gaining mastery over these five cybersecurity types extends beyond comprehending technical intricacies—it entails implementing strategies for a secure digital journey.Embracing these practices not only deepens your understanding but also strengthens defenses against ever-changing threats. This proactive approach guarantees a resilient digital presence, comprehensively safeguarding your online world against emerging cyber threats with a comprehensive shield..
FAQs
Q.Is cybersecurity a good career?
Ans. Absolutely, cybersecurity is a fantastic career choice with high demand, job security, and competitive salaries.
Q. How is cybersecurity used?
Ans. Cybersecurity is used to protect computer systems and data from unauthorized access and cyber threats through measures like encryption and security protocols.
Q.Is cybersecurity a good career?
Ans Absolutely, cybersecurity is a standout career choice, offering high demand, competitive salaries, and significant impact in securing digital environments.
Q. How do I learn cyber security?
Ans “Begin your cybersecurity journey with basics, online courses, and hands-on practice. Earn certifications, stay updated, and explore ethical hacking for a successful career.”
Blog by https://easyexpressxyz.com


4 thoughts on “what are five 5 types of cyber security”